As part of the Professional-Services packages we offer our clients, Cymulate’s security experts ran Lateral Movement campaign together with the clients. The main security misconfigurations our team identified were associated with the usage of golden images to deploy new servers and workstations.
The usage of golden images can help IT managers to easily deploy new endpoints in the network. By preconfiguring once, the IT team can rest assured the new endpoint will include all the necessary settings and configurations, without the need to configure each new endpoint every time. The problem starts, when the deployment procedure lacks changing the password of the local users on the new endpoint following the deployment.
By reusing the token of the local users, especially the local administrator user, a potential threat actor could easily move laterally and reach high risk network areas and critical assets. In severe cases, the Domain Controller’s local administrator password is reused as well, meaning the same password is used for the Domain Administrator user – and can lead to complete domain takeover.
The Lateral Movement campaign succeeded in identifying the vulnerability for a number of our customers, by escalating privileges on the local machine and reusing the token of the local Administrator account against other discovered machines in the network.
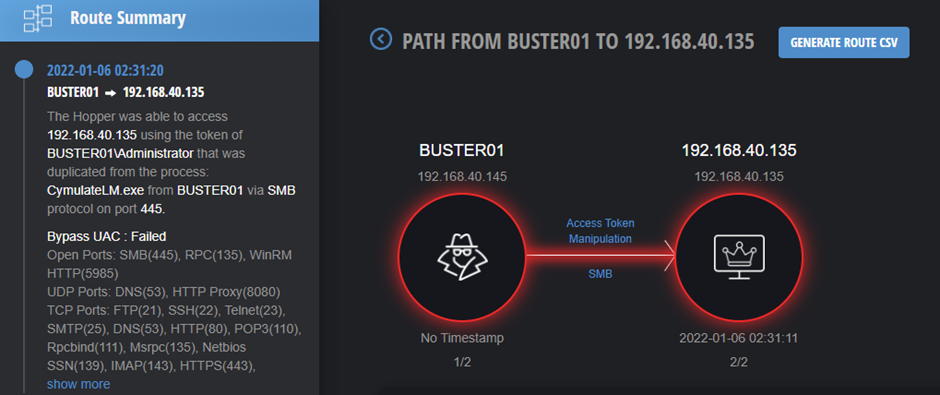
We can see the Cymulate Hopper (Cymulate’s Lateral movement campaign beacon) successfully breached the Domain Controller by reusing the Administrator token from the local machine, BUSTER01, gaining domain admin privileges. Important to note, this was done in a matter of a few minutes.
This technique, which is widely used by attackers in order to move laterally and escalate privileges in the corporate network, is one of the attack vectors the Cymulate Lateral Movement campaign uses in order to spread in the given scope.
In order to mitigate this security gap, it is necessary to give each endpoint’s accounts a different password. The password should be random and include symbols and numbers. It is recommended to deploy a password manager solution, such as Microsoft LAPS, to help manage the local accounts users’ passwords.



