MITRE just published the 11 Strategies for a World-Class Cybersecurity Operations Center book. A recurring theme in this book is the importance of Cyber Threat Intelligence (CTI) as instrumental to “augment the SOC’s ability to identify adversaries and discern their movements from those of authorized users.” The document further states that CTI “moves the SOC from a per-incident approach to an adversary-focused paradigm.”
As Cymulate for Exposure Management and Security Control Validation is designed to provide extensive in-context CTI capabilities and, as such, supports each one of these tactics as briefly broached below.
MITRE Strategy 1 - Know what you are protecting and why:
Exposure Management and Security Control Validation provides a continuously updated situational awareness of the security posture of individual attack vectors, including iteratively observing, orienting, deciding, and acting through:
- the creation and continuous updater of a composite inventory of all exposed assets through attack surface management,
- the continuous security posture assessment through production-safe attack simulation of all MITRE TTPs and emerging threats
- In-depth threat understanding with documented threat history and IoCs, complemented by mitigation recommendations.
- Continuous awareness building through overarching and granular trend analysis of security posture scores.
MITRE Strategy 2 – Give the SOC the Authority to Do its Job:
Cymulate Extended Security Posture Management platform uses hard-data-based scoring methods to provide the SOC with the required aggregate information and set metrics. The summarized data details situation-specific content.
MITRE Strategy 3 - Build a SOC Structure to Match Your Organizational Needs:
Exposure Management and Security Control Validation provides the tools to accurately evaluate any set of data risk posture, prevent security drift from agreed risk tolerance levels, and can flexibly adapt its SLA to the SOC’s constituency size.
When integrated with SIEM and SOAR tool stacks, Exposure Management and Security Control Validation production-safe attacks identify capability overlaps and security gaps, thus preventing wasted resourcing, limited SA, inadequate detection, reduced ability to investigate incidents, and insufficient response.
MITRE Strategy 4 - Hire AND Grow Quality Staff -
Exposure Management and Security Control Validation’s easy-to-use interface, dynamic dashboard with off-the-shelf attack scenarios and campaigns covering the entire kill chain and modulable templates greatly accelerate training adversarial skills, and the purple team framework empowers a traditional blue team with the tool to access purple teaming capabilities with limited additional training.
This directly addresses the Cyber Threat Intelligence conundrum delineated in MITRE Strategies point 4.5.4.
Exposure Management and Security Control Validation advanced VPT Attack Based Vulnerability Management further alleviates the Vulnerability scanning and assessment issues raised in points 4.5.5 and 4.5.6
MITRE Strategy 5 - Prioritize Incident Response:
Exposure Management and Security Control Validation gives the SOC team the ability to practice IR engagements utilizing all types of attacks based on MITRE ATT&CK Framework TTPs. This allows the SOC to become more proficient in the response or action to an incident. It also enables the SOC to build the incident prioritization plan around the priority level and response based on the incident or event.
MITRE Strategy 6 - Illuminate Adversaries with Cyber Threat Intelligence:
By continuously operationalizing MITRE ATT&CK structured contextualized TTPS, as well as emerging threats, Exposure Management and Security Control Validation provides SOCs with actionable, timely, relevant, and accurate CTI, enriched with built-in correlation with the risk posed to your environment.
Selecting between the technical or executive automatically generated reports enables SOC to immediately further relevant information to stakeholders ranging from the IT team tasked with implementing the mitigation recommendation to executives relying on timely information to make informed decisions.
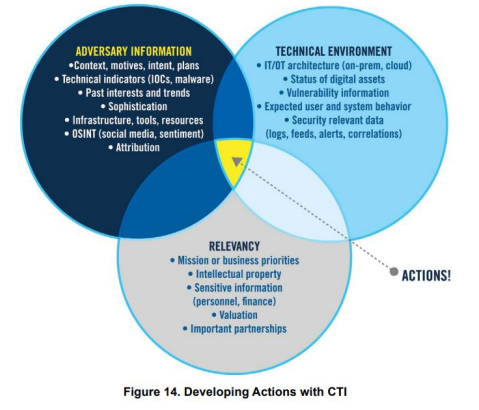
By default, Exposure Management and Security Control Validation dashboards find the convection point between Adversary information, technical environment, and relevancy to highlight recommended actions. More in-depth insights can easily be extracted using Cymulate customizable dynamic dashboards to find correlations specifically relevant to individual situations.
MITRE Strategy 7 - Select and Collect the right data:
Cymulate's Exposure Management and Security Control Validation platform integrates directly into your security stack to scrape the events/ alerts created when a production-safe attack is executed from the platform. These events/alerts are then incorporated into the Exposure Management and Security Control Validation dashboards, providing the SOC analyst direct access to the data and at-a-click modular correlation options between different data sets and visualizing them displayed in various formats with diverse properties. XSPM also validates whether attacks are detected by the SIEM and either generates an automated response or raises alert to ensure prompt human action.
MITRE Strategy 8: Leverage tools to support analyst workflow:
As Exposure Management and Security Control Validation integrates with SIEM and SOAR and provides direct, measurable information about the security gaps uncovered during continuous security validation processes, and provides default and customizable dynamic dashboards, the analysts can streamline their workflow using built-in widgets to select the data to visualize, trend or correlate it with other data.
MITRE Strategy 9 - Communicate clearly, collaborate often, share generously:
Cymulate’s platform automatically generates reports designed to present a clear picture of findings in different formats to technical teams and executives, promoting clear communication and collaborative goal settings.
MITRE Strategy 10 - Measure performance to improve performance:
Exposure Management and Security Control Validation hard-fact-based metrics and built-in trend analysis capabilities are designed to provide the information needed to ensure performance is continuously improved.
This includes improving the performance of the SIEM and SOAR solutions array as it provides granular information about the remaining security gaps, complete with actionable remediation advice, leading to a continuous optimization of security controls configuration.
MITRE Strategy 11 - Turn up the volume by expanding SOC functionality:
In addition to the off-the-shelf scenarios and campaigns that can be run by a blue team member with minimal additional training, Cymulate's Exposure Management and Security Control Validation platform provides an Advanced Purple Teaming Framework enabling users to reap maximum benefit from the built-in threat hunting, red teaming, purple teaming, Breach and Attack Simulation and Tabletop exercises
This is only a brief overview of how Cymulate’s Exposure Management and Security Control Validation aligns with MITRE strategies. Still, I would like to add that, from MITRE’s perspective, the last strategy pinpoints Breach and Attack Simulation and seems to imply that you are a "mature organization" when you get to this point.
I respectfully disagree. You do not have to be a mature organization in order to validate your compensating controls. User-friendly BAS technology can be easily integrated long before reaching maturity, and Cymulate’s Exposure Management and Security Control Validation modularity is designed to accelerate any company maturation process, independently or with a dedicated advisor through the Amplify program.
Bio: Arron Harrell is a Sr. Sales Engineer for Cymulate. He has spent 23 years in the cybersecurity space as an SE and SE leadership. Arron's list of passions is numerous, from cybersecurity validation to his dogs, to wildlife conservation. He's an avid hunter and fisherman and loves anything outdoors. Arron lives on an off-grid 50-acre farm an hour outside of Dallas, Texas, where he enjoys every aspect of country living.

