One of Cymulates greatest features is the Purple Team module. It allows users to create advanced attack scenarios for Threat Hunting scenarios using templates which are the chained sum of the plethora of executions created by Cymulate. Bundled with the Immediate Threat Module, one can create strong Threat Hunting scenarios.
But how does one create good threat hunting scenarios and really challenge ones Blue Team and test their capabilities?
The Pyramid of Pain
Let’s look at the pyramid of pain from a great article written way back in 2014.[1]
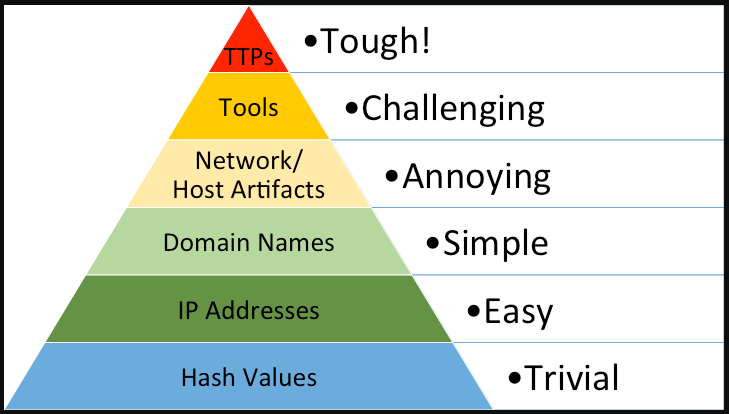
Designed back in 2013, as a response to the APT 1 report written by Mandiant[2]. It was created as a response to the discussion about the report – people were talking mostly about the host-based indicators and the network-based indicators detection instead of leveraging the information describing the TTPs reported within the report.
In short –
Hash values – the computed hash values for malware and tools dropped in a compromise, these can be added into your EDR based systems, but won’t really force the actor to change his behaviors as these hash values can change with the threat actor just flipping one bit in his tools.
IP Addresses – The IP addresses the threat actor used as Command & Control or just endpoints which the threat actor connected from to perform the intrusion. This can also be blocked and introduced into your detection tools but won’t hurt the Threat Actor as IP addresses can be easily changed and moved. Consider a threat actor connecting to your network through a VPN server, its highly probable that the IP addresses that connected from the same server on one day, will change on the other day.
Domain Names – The domains that the actor hosted his Command & Control server or his malicious infrastructure. Blocking these might hurt but just as well be slight annoyance to the actor as new domains can be bought and registered anonymously with relative ease.
Network & Host Artifacts – We’re getting into the yellow zone, these are artifacts found within an intrusion such as User-Agent strings, Unique binary signatures (corrupted file headers for example), Unique strings found in packets or malware. Triggering detections on these kinds of events using Yara-Rules for example will force the threat actor to recompile or rebuild his tools. At this level, we’re causing the threat actor some pain.
Tools – In the purple area we have tool detection, say the threat actor exclusively uses PowerShell or VBS scripts. If your detection teams can block and detect manual execution of abnormal PowerShell or VBS scripts (or just block them entirely within your organization) will force the threat actor to find new tools, research them and learn how to efficiently use them. This hurts, this takes time and energy to learn causing the Threat Actor to perhaps just skip attacking your organization.
Tools, Techniques & Procedures – Once you respond at this level - not just detecting the actors Tools, but his entire behavioral patterns you force the actor to learn new behaviors as in change his entire playbook. Consider the Conti Playbook [3] which was leaked describing the entire playbook of the affiliates who spread the Conti ransomware strain. The leak caused a major blow to Conti affiliates as their entire playbook was published, describing their entire intrusion plans which they mostly copy pasted in intrusions causing them having to re-learn new behaviors entirely.
Using Cymulate, we can test our environment throughout the entire Pyramid as we can simulate attacks using the Immediate Threat module which will target the low end of the pyramid until the mid-end, and we can use the Purple Team Module to address the high level of the pyramid.
The next question that we should address is what kind of threats should we protect ourselves from? All threats? Every single APT? That would be time consuming. This brings us to the next part.
Threat Diamond Model
Before creating a Threat Hunting simulation, we need to create some sort of hypothesis for our threat hunt. You should know what threats are out to get your organization. We can leverage the Diamond threat model to do this.
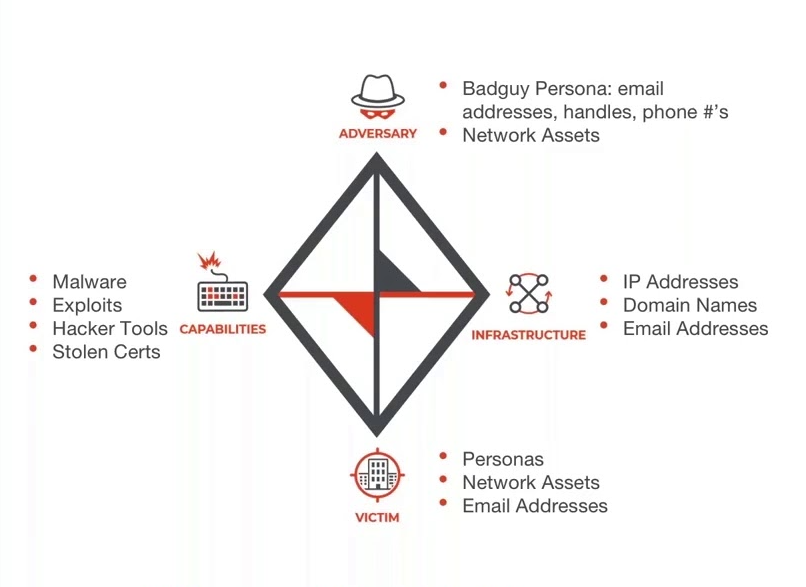
credit goes to threatconnect.com
Before filling up the model you should consider what kind of threat actor would consider attacking your organization by asking:
- “What is my geolocation?”
- “What are my strategic assets?”
- “What sector am I part of?”
- “How big is my organization?”
Let’s assume I am an organization in the America, I am part of the Fintech sector, my strategic assets are Insurance databases and I’m a big organization with a high revenue return.
Using https://www.mandiant.com/resources/apt-groups and https://attack.mitre.org/groups/ we can easily search for possible threats. By simply searching the word ‘financially’ we can find several groups. I am going to choose Wizard Spider for this specific example.
Next, I would research the internet to find all possible information regarding this group that would help me fill up the Diamond Model mentioned above.
Here’s an example of how I filled up the Diamond Model –
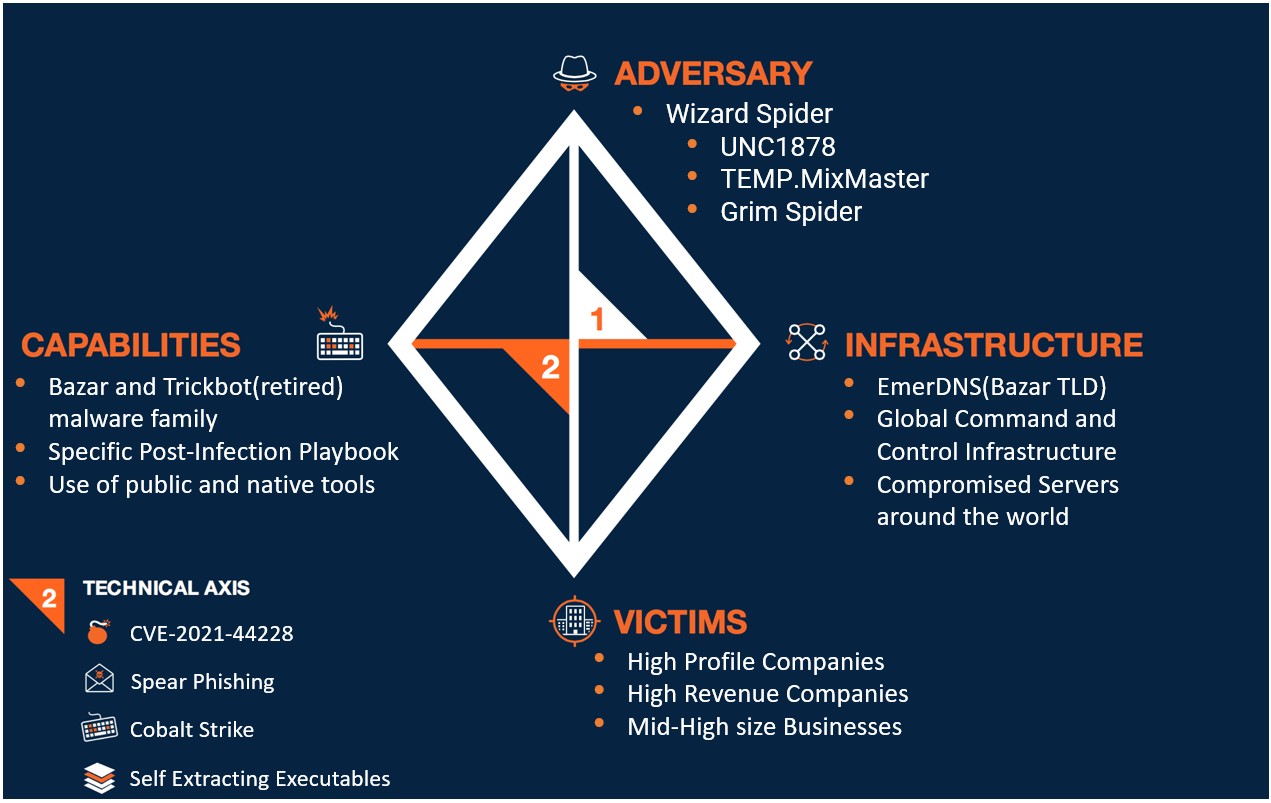
The above model is based off the ThreatConnect.com model and examples and should be taken with a grain of salt but it should serve its purpose as an example for you.
Now that we are aware of which actor we want to hunt, we can begin simulating an attack scenario.
Points for creating a quality attack template for a Threat Hunt Simulation
Besides using the templates created by Cymulate, users can create their own templates. Here’s some pointers for creating quality templates.
Base templates on real intrusions
Quality simulations try to mimic the real events as much as possible. Try to locate real intrusions online which have mapping to the MITRE ATT&CK matrix.
Good sources for this include:
Use chained executions in your templates
Leverage the chaining option in templates to mimic chained operations such as exfiltration or lateral movement. Chaining allows you to chain two or more executions together allowing the executions to pass information and data to each other. This behavior will simulate and mimic behavior in a more realistic way.
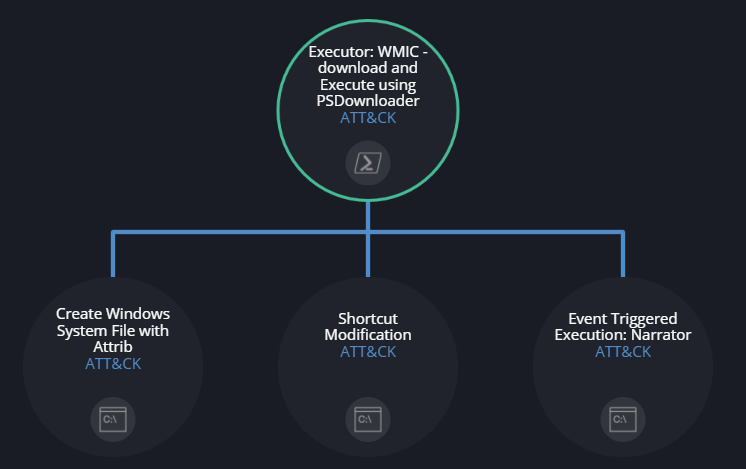
example of a chained executions in the available Lazarus APT template
In the above example, three different executions take input from the results outputted from the “WMIC” executor.
Prepare your environment for intrusions
Make your environment realistic as possible, with settings that mimic of real workstations in your network so you can truly test the value of the Security Systems and test the skills of your Security Team.
Leveraging the Immediate Threat module
The Immediate Threat module is great for hitting the low-mid ends of the Pain Pyramid. The Immediate Threat module is constantly updated by the Cymulate team. However, it can also be enriched by your security team.
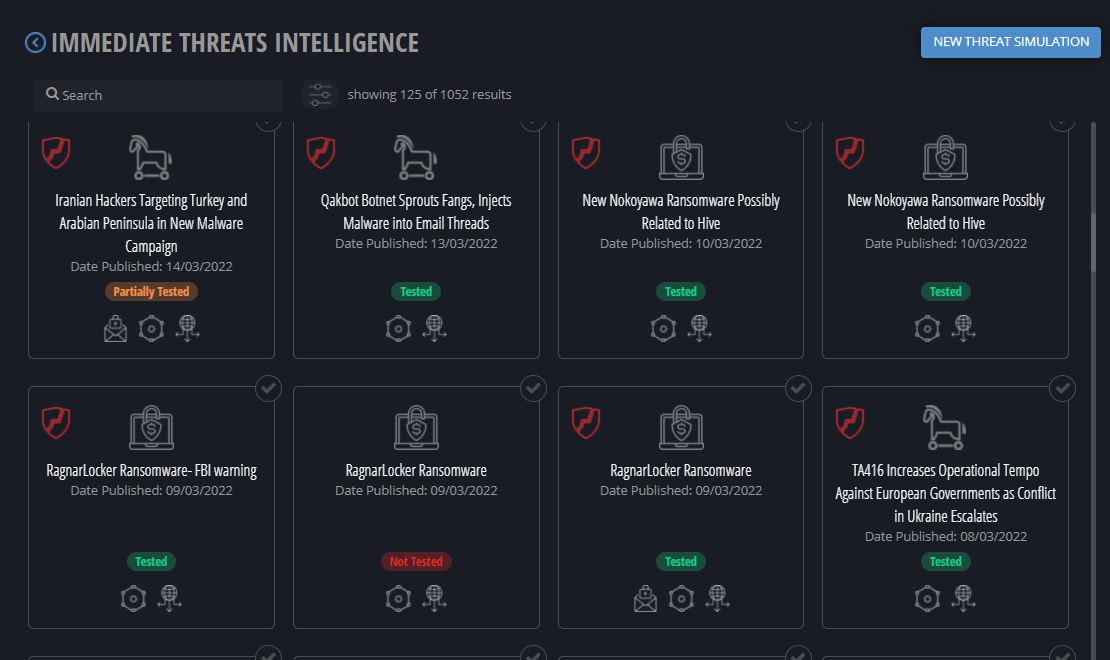
This module allows you to simulate an intrusion by dropping IoCs from real intrusions. Simply choose a real intrusion found online, found in blog posts around the internet and upload the findings to the module.
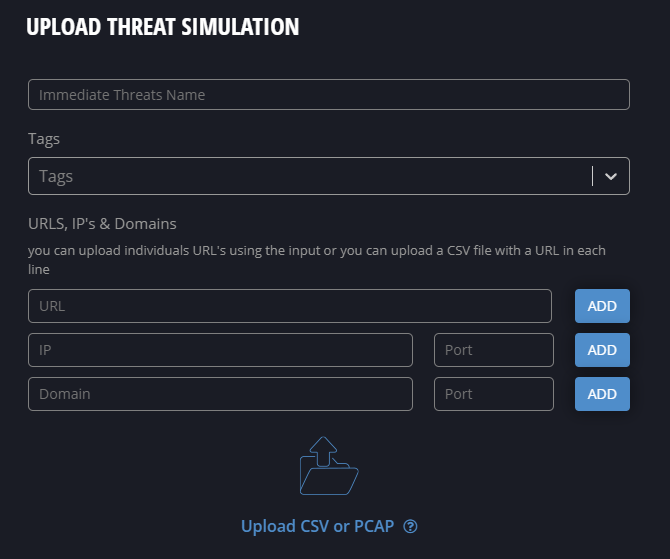
Once you uploaded your own event (or used the ones available) you can launch it on a selected endpoint.
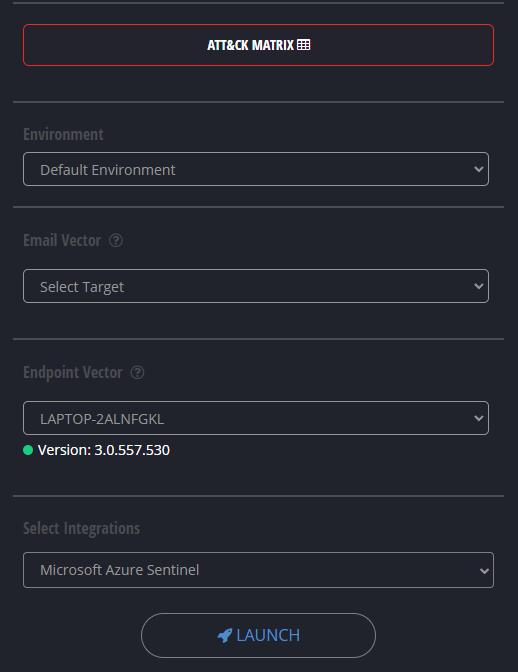
This will drop the IoCs which were uploaded by you onto the system. The Cymulate agent will not execute them but only drop them on the endpoint to check if they are detected by your security products. Additionally, Network based IoCs will be probed in a safe way to see if it triggers your security system.
That’s its folks, see you next time.




