Halloween is on the horizon, but a far spookier threat lurks online, targeting businesses and governments worldwide. I'm talking about the elusive cybercriminal group known as the Silence Group. Let me tell you about their spine-chilling tactics.
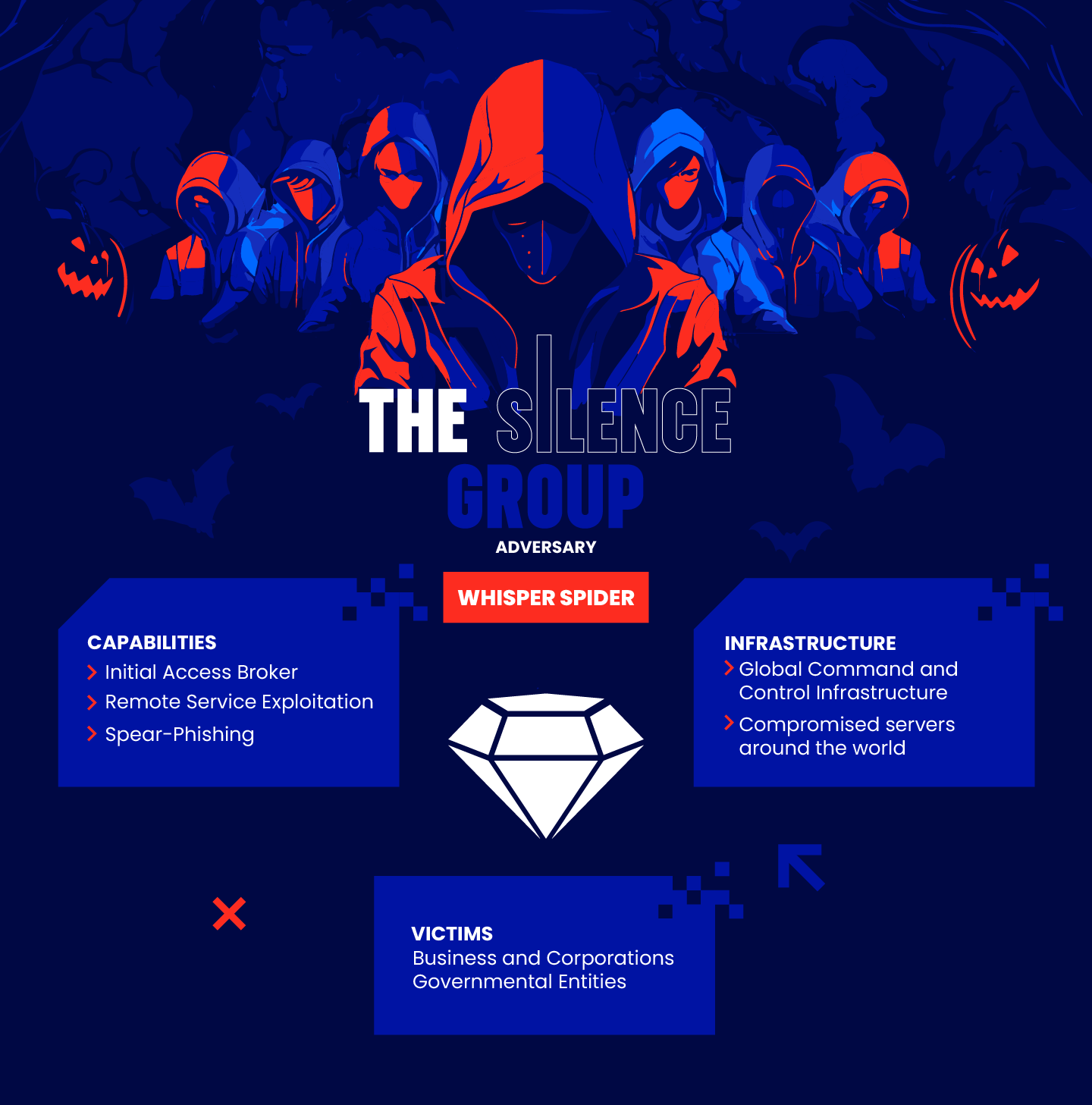
Emerging in 2016, the Silence Group, also known as Truebot, has been infiltrating networks, spying on operations, and stealing sensitive data and funds. They initiated attacks through phishing, including appear-phishing that included malicious attachments, hoodwinking target organizations’ employees. They also use remote service exploits to gain initial access. The phishing malicious attachments masquerade as Microsoft Office docs or help files. If opened, they trigger secret scripts that let the attacker in.
Today, the Silence Group infrastructure includes global command and control capabilities and direct access to compromised servers across the globe. Given this hyper focused asset bank and capability set, the Silence Group has become an initial access broker.
This means that, instead of running an attack full kill-chain for themselves, they sell their ability to infiltrate targeted infrastructure. This enables the malicious actors purchasing the Silence Group services to focus on perfecting their own malware and exploits instead of devoting resources to developing initial access methods. The result is the creation of a supply chain similar to SAAS in the non-criminal world.
In that underground marketplace, malevolent actors can buy and sell all kinds of nefarious services, each matching a specific domain of expertise.
In late 2022, for example, the Lace Tempest group, infamous for deploying the Clop ransomware, encrypting their victims’ networks until a ransom is paid. Another group, Evil Corp, is also known to use the Silence Group services to get access to the targeted organization, and then take over it to deploy their various strands of ransomware.
Tactics, Techniques, and Procedures
Silence, also recognized by its other name, Truebot, is a malware downloader that has been under construction since 2017. The malware has the ability to gather data from infiltrated systems, establish communication channels (C2) with the cyber attackers, and execute additional payloads such as Cobalt Strike Beacon. This is frequently seen in cyber intrusions that culminate in the deployment of ransomware.
As of late 2022, a cybercrime collective known as Lace Tempest (DEV-0950), infamous for utilizing Clop ransomware, has been noted to exploit Truebot. To disseminate Truebot, Lace Tempest employs a multitude of assault vectors, including Raspberry Robin contaminations which have been observed since October 2022, as well as taking advantage of zero-day and one-day vulnerabilities.

As its name indicates the Silence Group is, well, silent. This means that as a gate cracker, it stealthily opens a crack in organizations’ defense mechanisms, ushers in its clients and vanishes, their job completed.
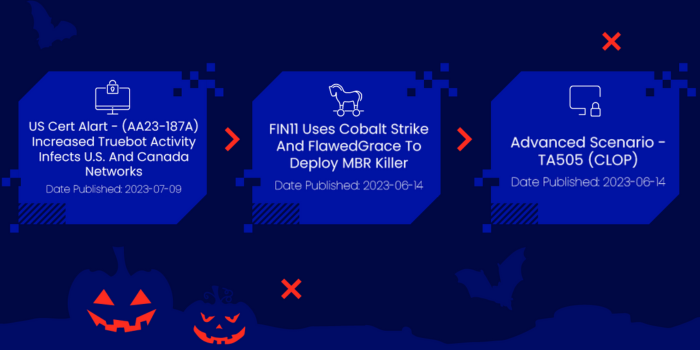
Luckily, a large number of their practices is well documented. This enables organizations to check whether their infrastructure is vulnerable to the Silence Group, or if they should preemptively fix identified security gaps.
Cymulate already offers two immediate threats and one advanced scenario designed to simulate infiltration methods used by the Silence Group and identify defense system weaknesses.
So while you enjoy Halloween this year, beware of the lurking Silence Group.
Stay safe out there and have a spooky Halloween! 🎃
Dan Lisichkin
Threat Hunter and Threat Intelligence Researcher at Cymulate



